
Phishing, one of top 8 Cyberthreats to marine & offshore Organisation
What is phishing?
Phishing is a type of online scam where criminals impersonate legitimate organisations via email, text message, advertisement, or other means to steal sensitive information.
Examples of specific phishing risks and their consequences to the shipping industry
Spear phishing emails – requesting payment or goods to be sent to a seemingly familiar and/or legitimate destination.
• Eg. a PDF attachment titled ‘Mearskshippingdetails.pdf’ was sent to attempt to replicate the way the legitimate service operates. This was not related to their communications or a vulnerability within Maersk, but rather an attempt by a threat actor to use their name to legitimise the phishing email being sent. It is an indication that threat actors will use the reputation and name of some of the well-known companies within marine and offshore.
• An email attempting to impersonate a “Maersk” employee using a subject line of “Maersk New Shipping schedule details due to COVID-19- Shipment notification.” The sender included “Maersk” and “COVID-19” in the subject line to trigger the recipient to believe the message was urgent and related to the current Corona Virus Pandemic.
In another malicious email, with subject line “COVID-19 SUSPECTED CREW /VESSEL.” analysts saw the World Health Organization being leveraged to spread malware with two malicious attachments; a MS Word document and MS Excel spreadsheet. Both were detected as malicious by Antivirus software. The sender and recipient email addresses were shown as alias’ but otherwise appeared legitimate.
Consequences – Damage to reputation, delay, monetary, identity theft and financial losses.
5 Common Features of Phishing Emails
Too Good to Be True – Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately.
Sense of Urgency – A favourite tactic amongst cybercriminals is to ask you to act fast because the super deals are only for a limited time. Sometimes, they will tell you that your account will be suspended unless you update your personal details immediately. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet.
Hyperlinks – A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different, or it could be a website with a misspelling, for instance www.marinearnerica.com – the ‘m’ is actually an ‘r’ and an ‘n’, so look carefully.
Attachments – If you see an attachment in an email you were not expecting or that does not make sense, do not open it! They often contain payloads like ransomware or other viruses. The only file type that is always safe to click on is a .txt file.
Unusual Sender – Whether it looks like it is from someone you do not know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general do not click on it!
Phishing Techniques
There are several different techniques used to obtain personal/confidential information from users. As technology becomes more advanced, the cybercriminal’s techniques being used are also more advanced.
Pear Phishing
While traditional phishing uses a ‘spray and pray’ approach, meaning mass emails are sent to as many people as possible, spear phishing is a much more targeted attack in which the hacker knows which specific individual or organization they are after. They do research on the target to make the attack more personalized and increase the likelihood of the target falling into their trap.
Email/Spam
Using the most common phishing technique, the same email is sent to millions of users with a request to fill in personal/confidential details. These details will be used by the phishers for their illegal activities. Most of the messages have an urgent note which requires the user to enter credentials to update account information, change details, or verify accounts. Sometimes, they may be asked to fill out a form to access a new service through a link which is provided in the email.
Phishing through Search Engines
Some phishing scams involve search engines where the user is directed to products sites which may offer low-cost products or services. When the user tries to buy the product by entering the credit card details, it is collected by the phishing site. There are many fake bank websites offering credit cards or loans to users at a low rate, but they are phishing sites.
Vishing (Voice Phishing)
In phone phishing, the phisher makes phone calls to the user and asks the user to dial a number. The purpose is to get personal information of the bank account through the phone. Phone phishing is mostly done with a fake caller ID.
Smishing (SMS Phishing)
Phishing conducted via Short Message Service (SMS), a telephone-based text messaging service. A smishing text, for example, attempts to entice a victim into revealing personal information via a link that leads to a phishing website.
Link Manipulation
Link manipulation is the technique in which the phisher sends a link to a malicious website. When the user clicks on the deceptive link, it opens the phisher’s website instead of the website mentioned in the link. Hovering the mouse over the link to view the actual address stops users from falling for link manipulation.
12 Ways to Avoid Phishing Scams:
To prevent Internet phishing, users should have knowledge of how the bad guys do this and they should also be aware of anti-phishing techniques to protect themselves from becoming victims.
There are some things that you can do to protect yourself and the organization:
1. Install an Anti-Phishing Toolbar – Most popular Internet browsers can be customized with anti-phishing toolbars. Such toolbars run quick checks on the sites that you are visiting and compare them to lists of known phishing sites. If you stumble upon a malicious site, the toolbar will alert you about it. This is just one more layer of protection against phishing scams, and it is completely free.
2. Implement strong email defences – consider installing a mail filtering system and blocking emails containing features your business does not need (for example macro-enabled Office documents) and install mail filtering software.
3. The browser settings should be changed to prevent fraudulent websites from opening. Browsers keep a list of fake websites and when you try to access the website, the address is blocked, or an alert message is shown, and security patches are released for popular browsers all the time. They are released in response to the security loopholes that phishers and other hackers inevitably discover and exploit. The settings of the browser should only allow reliable websites to open.
4. If there is a link in an email, hover over the URL first and visit only secure websites with a valid Secure Socket Layer (SSL) certificate begin with “https”.
5. Provide security awareness training for staff who send and receive emails.
6. Monitor networks to detect malicious traffic, and systems to detect unusual access or data access.
7. Make sure security updates are promptly applied to systems that deal with data or messages from untrusted sources.
8. Use Firewalls – Firewalls act as buffers between you, your computer, and outside intruders. You should use two different kinds: a desktop firewall and a network firewall. The first option is a type of software, and the second option is a type of hardware. When used together, they drastically reduce the odds of hackers and phishers infiltrating your computer or your network.
9. Beware of Pop-Ups – Pop-up windows often masquerade as legitimate components of a website. All too often, though, they are phishing attempts. Many popular browsers allow you to block pop-ups; you can allow them on a case-by-case basis. If one manages to slip through the cracks, don’t click on the “cancel” button; such buttons often lead to phishing sites.
Instead, click the small “x” in the upper corner of the window.
10. Use Antivirus Software – Special signatures that are included with antivirus software guard against known technology workarounds and loopholes. Just be sure to keep your software up to date. New definitions are added all the time because new scams are also being dreamed up all the time. Anti-spyware and firewall settings should be used to prevent phishing attacks and users should update the programs regularly.
11. Verify a Site’s Security – Before submitting any information, make sure the site’s URL begins with “https” and there should be a closed lock icon near the address bar. Check for the site’s security certificate as well. If you get a message stating a certain website may contain malicious files, do not open the website. Never download files from suspicious emails or websites. Even search engines may show certain links which may lead users to a phishing webpage which offers low-cost products.
12. Think Before You Click! – It’s fine to click on links when you’re on trusted sites. Clicking on links that appear in random emails and instant messages, however, is not such a smart move. Hover over links that you are unsure of before clicking on them. when you click the link to the website, it may look exactly like the real website. The email may ask you to fill in the information, but the email may not contain your name. Most phishing emails will start with “Dear Customer” so you should be alert when you come across these emails. When in doubt, go directly to the source rather than clicking a potentially dangerous link.
You don’t have to live in fear of phishing scams. By keeping the preceding tips in mind, you should be able to enjoy a worry-free online experience.
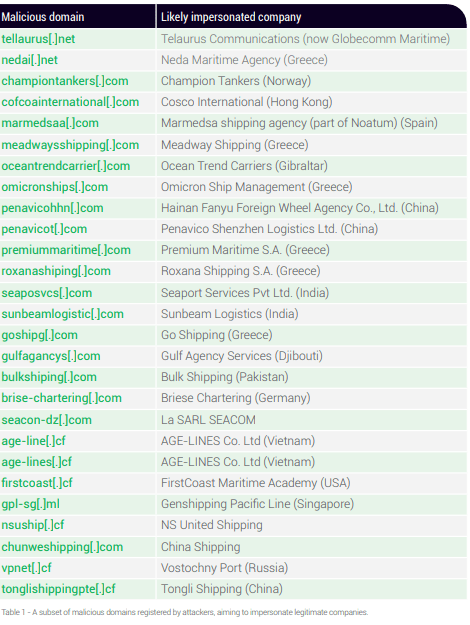
Below are the examples of malicious domain of Maritime Industry
Reference
https://dryadglobal.com/maritime-cyber-security-threats-2-2/
https://globalmaritimehub.com/wp-content/uploads/attach_908.pdf
https://blog.nettitude.com/the-top-8-cyberthreats-to-marine-and-offshore-organisations-part-1-phishing-and-physical-infiltration



